Sommaire
Introduction
Domain names have become much more than simple Internet addresses: they are essential tools for visibility, image, and trust for companies. At the same time, this strategic importance has made domain names a prime target for counterfeiters, scammers, and impersonators of all kinds.
Infringements on trademarks through domain names, whether in the form of cybersquatting, phishing, or sophisticated commercial scams, are proliferating as technology makes them easier to implement, faster to execute, and harder to trace. These practices threaten the value of trademark portfolios, consumer safety, and corporate reputations.
In this context, it is crucial to understand the various forms of abuse, the legal remedies available to address them, and the importance of an active domain name monitoring strategy.
Understanding the main types of trademark infringement via domain names
1.1. Cybersquatting: hijacking a brand for speculative purposes
Cybersquatting involves registering a domain name corresponding to a trademark, with the intent to resell it to the rightful owner or benefit from its notoriety. This practice has become industrialised with the publication of public databases such as those of the EUIPO or USPTO, allowing some actors to automate targeted registrations immediately after a new trademark is published.
1.2. Typosquatting: typing errors as a fraud tool
Typosquatting is based on deliberate spelling variants or typing errors, exploiting user mistakes to redirect them to fraudulent sites or advertising pages. This technique is especially used to capture traffic for commercial purposes or to host malware.
For instance, a user typing “microsfot.com” instead of “microsoft.com” might be redirected to a site containing a virus or a fake update to download.
1.3. Phishing and spear phishing: digital identity theft
Phishing involves mimicking an official site to extract personal or banking data. The domain name used usually reproduces the brand or a credible variant. This practice is often paired with fraudulent emails that redirect to the fake site.
Spear phishing is more targeted, aimed at internal employees or business partners for fraudulent purposes (e.g. fake wire transfer requests).
For example, registering a fraudulent domain name mimicking a bank to host a cloned site asking the user to “update” their banking details.
1.4. Employment, order, or fake shop scams: complex schemes
Numerous fraudulent schemes now rely on domain names to give false legitimacy to fake e-commerce sites, recruitment platforms, or customer service portals. The domain name becomes a central tool of deception.
- Counterfeit sales websites or fake shops: sophisticated imitation of an official site to sell counterfeit products or obtain banking data.
- Identity theft and purchase order scams: domain names similar to procurement centres used to extract money or divert goods.
Responding effectively to the hijacking or abusive use of a domain name
2.1. Resorting to specialised out-of-Court procedures
Some administrative procedures allow for the deletion or transfer of a domain name without going through the courts. These are particularly useful when the infringement is clear and the domain name holder is difficult to locate or operates abroad.
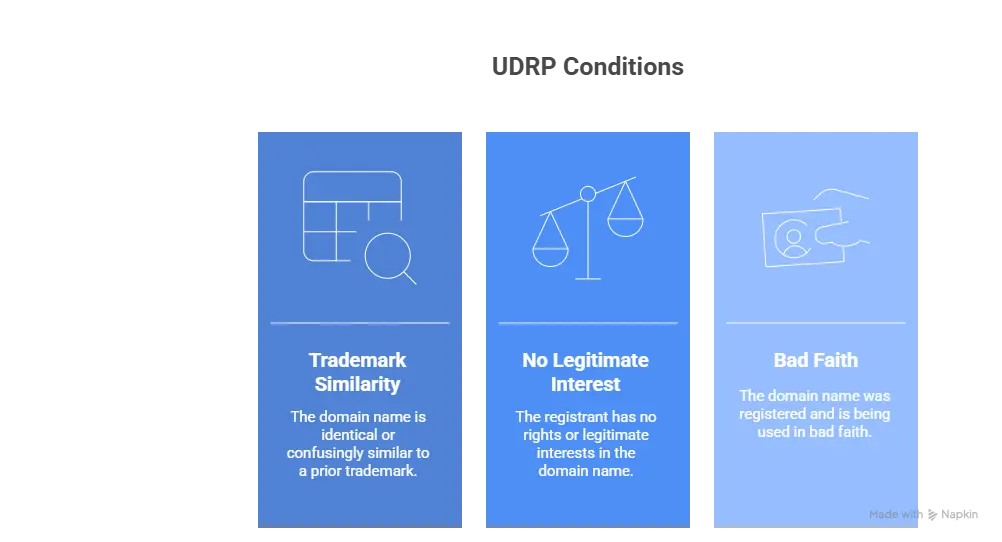
- UDRP (Uniform Domain-Name Dispute-Resolution Policy)
Managed notably by the WIPO Arbitration and Mediation Center, this international procedure applies to most generic extensions (.com, .net, .org, etc.). It allows for the transfer or cancellation of a domain name when three conditions are met:
-
- The domain name is identical or confusingly similar to a prior trademark;
- The registrant has no rights or legitimate interests in the domain name;
- The domain name was registered and is being used in bad faith.
- Syreli (AFNIC)
This procedure applies to .fr domain names and is administered by AFNIC. It has the advantage of being fully digital, faster than a traditional trial, and results in a decision within two months.
- URS (Uniform Rapid Suspension System)
A simplified alternative to the UDRP, it targets clear-cut cases of cybersquatting. It is especially suitable for quickly suspending a domain name, without obtaining its transfer, when the infringement is blatant and well-documented.
- Cease and Desist Letter: a tool not to be overlooked
Sending a cease and desist letter formalises a request for withdrawal or transfer, demonstrating the prior rights and abusive nature of the use. This approach is often combined with technical notices (to registrars, hosts, or platforms). In simple cases, it can suffice to achieve a swift amicable resolution, particularly when the registrant is not an experienced professional.
2.2. Judicial actions: for serious or unresolved infringements
When out-of-court procedures fail or are not appropriate, legal action can be taken.
- Identifying the registrant: Article L.34-1 of the French Postal and Electronic Communications Code.
This provision allows, via summary proceedings, to obtain information from the registrar or hosting provider, lifting the veil on the identity of a domain name holder or site administrator.
- Trademark infringement or unfair competition actions :
If the domain name use infringes a registered trademark, a trademark infringement action is available. If the mark is not registered, it is still possible to act based on unfair competition or parasitism, by demonstrating abusive appropriation of another’s reputation.
2.3. Engaging the right intermediaries
In the technical domain name ecosystem, third-party actors play a key role in putting an end to infringements.
- The Registrar : They manage domain name reservations. When served with a UDRP decision or court injunction, they can block, suspend, or transfer the domain.
- The Hosting Provider : They host the content displayed under the domain name. In case of unlawful content, they can be served with a formal notice to remove it, under penalty of liability.
2.4. Gathering evidence: a prerequisite for any action
An effective response requires thorough documentation of the facts. The following should be collected and preserved as soon as the infringement is detected:
- Whois Data: to identify the holder or technical contact of the domain name.
- Screenshots of the infringing site, including the full URL, date, time, and infringing visual or textual elements.
- Fraudulent emails or technical logs: in case of phishing or misuse of email servers configured on the infringing domain.
- Correspondence with technical providers: can demonstrate inaction from a host or registrar, useful in liability proceedings.
Implementing proactive monitoring to protect assets over the long term
3.1. Domain name watch services to prevent infringements
Anticipate before damage occurs
Automated domain name monitoring relies on alert systems analysing in real time new creations in WHOIS databases, DNS registration bases, or root server zones. These tools signal domain registrations that closely resemble a protected trademark:
- Addition or removal of a character
- Letter inversion or homographs
- Registration in an unusual extension (.shop, .buzz, .store, etc.)
Detecting a malicious domain name upon registration, before a site is put online or promoted through search engines, enables preventive action that is often quicker and less costly.
3.2. Implementing a global defensive strategy: monitor, register, neutralise
Register strategic names in advance
An effective strategy combines monitoring and registrations. It is not about registering all possible domain names, but targeting the most sensitive extensions and variants:
- High-traffic generic extensions: .com, .net, .shop, .store, .vip
- Local extensions of key markets: .fr, .de, .cn
- Extensions prone to misuse: .xyz, .top, .online, .buzz
Defensive registrations help secure critical names before third parties can exploit them. This approach is especially useful during product launches, major events, or brand expansions.
Document to act more effectively
A solid monitoring strategy is supported by an evidence system: each alert must be documented by a screenshot, a timestamp, or a source code extraction if needed, to serve as a basis for UDRP or judicial action.
Conclusion
An effective brand strategy requires proactive domain name governance
in light of the growing scale of digital infringements, it has become essential to integrate domain names at the heart of your trademark protection strategy. Identify, respond, anticipate: these are the three steps to effective defence, based on appropriate legal tools, collaboration with the right technical actors, and continuous monitoring.
Dreyfus & Associés has been supporting companies of all sizes for over 20 years in the strategic, defensive, and contentious management of their domain name portfolios.
The firm works in partnership with a global network of Intellectual Property lawyers.
Nathalie Dreyfus, with the support of the entire Dreyfus team
FAQ
1. What is cybersquatting?
It is the abusive registration of a domain name identical or similar to a trademark, with the intention of reselling it or deriving undue advantage.
2. What procedures are available to recover a domain name?
The UDRP (international) or Syreli (for .fr) procedures allow for the transfer or deletion of the domain name.
3. How can I find out who registered a domain name?
By consulting the Whois service, although some data may be hidden. Further (judicial) actions may be necessary.
4. What if the registrar or host refuses to act?
Turn to judicial or administrative procedures, depending on the case. Article L.34-1 of the French CPCE can provide for investigatory measures.
5. How can fraudulent domain names be detected?
Through automated monitoring and alert tools that flag registrations similar to your trademarks.